After the first whitepaper surfaced on the internet in 2008, blockchain technology has evolved enormously. Founders, developers, and blockchain enthusiasts have proposed varying ideas on how the technology should function. However, there seem to be several underlying foundations and principles for blockchain technology despite the various prototypes. Let’s look at blockchain technology through the lenses of privacy and security.
Privacy
Blockchain technologies function as distributed ledger technology - a publicly encrypted network ledger shared across multiple nodes requiring a consensus mechanism to validate transactions. Consequently, every transaction is recorded on the blockchain and can be viewed at any time by any party. The identity of every individual is represented by a wallet address, hence the term “Pseudo-anonymous.”
The first privacy feature of any blockchain network is that all transactions are pseudo-anonymous. Every user has a public wallet address, owns a private key to the wallet, and there is a ledger where every wallet and their transactions are recorded and displayed publicly.
Security
We need to consider two questions when discussing security. First, how do blockchain users protect themselves? Secondly, how is a blockchain network as a whole protected from external attacks?
The seed phrase and a private key are necessary to safeguard the user in any decentralized blockchain network. A seed phrase is a specific number of words generated by a crypto wallet upon creation (whether it be a software or hardware wallet). A seed phrase may be twelve words, twenty-four words, or fifteen words, as is the case in the Ergo blockchain. A private key is a long string of hexadecimal numbers required to sign every transaction made by a wallet. In practice, a seed phrase encodes a private key and is the gateway to a wallet.
Every blockchain network is protected by a decentralized protocol of verifying transactions known as the consensus mechanism. Since Bitcoin’s emergence, blockchain networks have been built on varying consensus mechanisms. Broadly, the three most common consensus mechanisms are: Proof of Work (PoW), Proof of Stake (PoS), and Delegated Proof of Stake (DPoS). Each model uses miners or validators to verify transactions and blocks.
Proof of Work vs Proof of Stake
The emergence of the Bitcoin whitepaper represented the beginning of the cryptocurrencies era, but left the door open to potential improvements. Over the past couple of years, there has been much debate between Bitcoin’s Proof of Work and the Proof of Stake consensus mechanisms.
In the Proof of Work (PoW) consensus mechanism, miners solve complex equations, the first miner to the new hash is rewarded and a new transaction is added to the block. With Ergo, the protocol is ASIC resistant and allows for miners to use commercial GPU hardware to participate in the network. However, in Proof of Stake (PoS), validators stake their cryptocurrency in the network. In turn, they are randomly selected to verify network transactions based on their stake in the network.
Ergo’s extended UTXO and Proof of Work
Founded in 2018, the Ergo Blockchain utilizes both the Proof of Work consensus mechanism and the extended UTXO model (similar to Bitcoin’s UTXO model). Ergo’s choice for PoW was made based on years of research and an understanding that the consensus mechanism still had room for development and improvement.
Ergo endeavored to optimize the PoW consensus while building on its strong security foundations. This, in combination with the implementation of smart contracts on extended UTXO are the core foundations of the Ergo blockchain.
Ergo and extended UTXO
The extended UTXO model is where a total of the unspent transaction outputs are recorded after each transaction. Bitcoin first introduced UTXO and in contrast to Ethereum’s shared global context where any account can modify, UTXOs are short-lived immutable data structures.
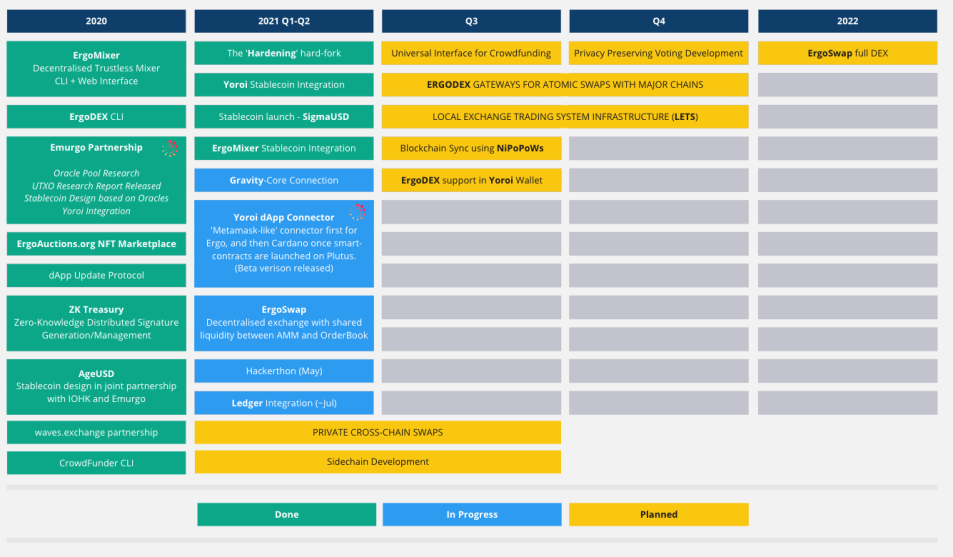
While UTXO offers a lot of privacy and even scalability reassurances, smart contract implementation is restricted on Bitcoin’s UTXO model. In Ergo’s case however, the UTXO was designed with ErgoScript to allow multi-stage contracts with zero-knowledge operations powered by Sigma Protocols. Ergo has Non-Interactive Proofs of Proof of Work (NIPoPoWs) support since the launch to allow for efficient light-clients and sidechains.
Ergo introduces read-only UTXOs to allow the formation of UTXO transaction chains. Summarily, Ergo’s extended UTXO is smart contract-enabled and it provides a platform for building dApps and DeFi tools maximizing the scalable design of UTXOs.
Ergomixer — A Tool for Privacy on Ergo
From implementing Sigma protocols on PoW consensus and the extended UTXO, the Ergo blockchain was built with privacy and security in mind.
Ergomixer is the first non-custodial, non-interactive mixer in blockchain. The privacy-based tool works like a physical wallet where a user can spend or perform a transaction without revealing their assets. The dApp is permissionless, enabling anyone on the Ergo blockchain to conceal private details when conducting transactions.
Ergo Summit: Privacy Week
As a community committed to the future of decentralization and issues in blockchain, Ergo will be hosting a privacy summit from February 17-23. The privacy summit features several keynote guest speakers who are experts in the industry and it will be hosted on Ergo’s Youtube channel. Every blockchain/DeFi enthusiast is invited to participate in the exciting upcoming summit!